NIS2
Network and Information Security (NIS2) Directive
Are you ready to raise your level of cybersecurity?
What is the NIS 2 Directive about?
NIS2 Directive for more cybersecurity
NIS 2, a directive within the European Union, is designed to establish a robust and uniform cybersecurity standard among EU Member States. Its primary objectives are to define fundamental cybersecurity risk management measures and reporting obligations applicable to critical sectors, thus eliminating disparities in cybersecurity requirements and their execution. Organizations falling under the ambit of NIS 2 should initiate early preparations, given that certain essential requirements may require considerable time to put into effect.
To comply with the NIS 2 Directive, EU Member States are required to adopt and publish the requisite measures by October 17, 2024.
Why NIS2?
A Better Version of NIS
The revision of the NIS Directive was prompted by its uneven implementation across Member States, resulting in a fragmented approach to cybersecurity. While some entities were classified as essential in certain countries, they were not recognized as such in others. To address these inconsistencies, the European Commission updated the directive, introducing the NIS2 Directive in 2021. This revision aimed to standardize the identification of essential organizations and clarify their obligations.
The NIS2 Directive significantly broadens the scope of its predecessor, extending its coverage to include a tenfold increase in the number of entities. It expands beyond the original sectors like water supply, energy, digital infrastructure, banking, health, and transport to encompass additional areas such as public administration, digital services, space, research, postal services, waste management, food, manufacturing, and chemicals.
Moreover, NIS2 enhances cybersecurity measures by enforcing early incident reporting, expanding risk management strategies, and establishing clear cybersecurity responsibilities at the executive level. This comprehensive approach not only ensures a more uniform application across the EU but also strengthens the overall cybersecurity posture of a wider range of sectors, making NIS2 a more robust version of the original directive.
Which entities come under NIS2?
The directive is applicable to organizations operating within the sectors listed below, provided they have a minimum workforce of 50 employees and/or a yearly turnover (and/or an annual balance sheet total) exceeding EUR 10 million. Nonetheless, there are certain exceptions where the size of the organization does not matter. Additionally, organizations subject to the CER Directive are automatically included under the NIS 2 Directive. The entities covered by this directive are categorized into two main groups:
- Critical Sectors: This includes organizations involved in financial market infrastructures, water supply, energy, digital infrastructure, transport (including air, rail, water, and road), healthcare, public administration, space, drinking and wastewater services, banking, and ICT-service management (covering managed service providers and managed security service providers).
- Other Critical Sectors: This category encompasses entities engaged in postal and courier services, waste management, the chemical sector, food industry, manufacturing of medical devices, computers and electronics, machinery and equipment, motor vehicles, trailers, semi-trailers, and other transport equipment, digital service providers, and research organizations.
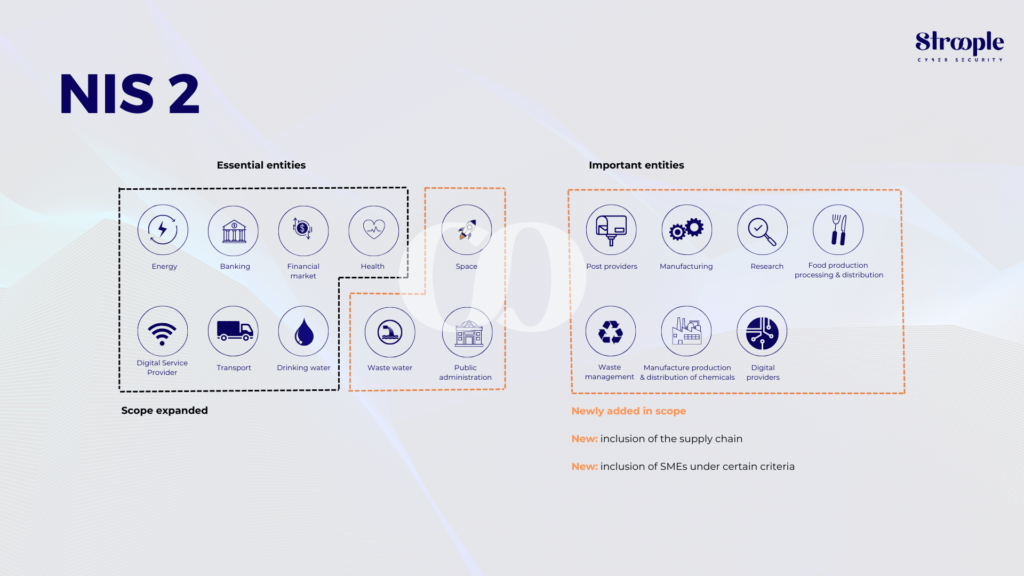
Organizations within the NIS 2 Directive’s remit are considered at minimum to be important entities. Typically, organizations with no fewer than 250 employees or an annual turnover above EUR 50 million and a balance sheet total over EUR 43 million are identified as essential entities. Essential entities are subject to more stringent oversight and regulatory measures compared to important entities.
What does the NIS2 Directive require?
A paradigm shift in cybersecurity and operational resilience
The NIS 2 Directive consists of four categories, incorporating a total of 23 measures, all stemming from the LPM’s themes.
To adhere to the NIS Directive, Operators of Essential Services (OES) and Digital Service Providers (DSPs) are required to implement adequate security measures and inform the appropriate National Competent Authorities (NCAs) or Computer Security Incident Response Teams (CSIRTs) about incidents causing significant disruption. Thus, to improve the security of network and information systems, the NIS Directive establishes an extensive framework that includes: governance at the level of Member States and their mutual cooperation, security obligations for OES and DSPs, impact evaluations using defined criteria, and the requirement for OES and DSPs to report incidents to the relevant NCAs or CSIRTs.
NIS2 Requirements | 10 Minimum Measures to Address
In addition to the four overarching areas of requirement, NIS2 mandates that essential and important entities implement baseline security measures to address specific forms of likely cyberthreats. These include:
- Risk assessments and security policies for information systems
- Policies and procedures for evaluating the effectiveness of security measures.
- Policies and procedures for the use of cryptography and, when relevant, encryption.
- A plan for handling security incidents
- Security around the procurement of systems and the development and operation of systems. This means having policies for handling and reporting vulnerabilities.
- Cybersecurity training and a practice for basic computer hygiene.
- Security procedures for employees with access to sensitive or important data, including policies for data access. Affected organizations must also have an overview of all relevant assets and ensure that they are properly utilized and handled.
- A plan for managing business operations during and after a security incident. This means that backups must be up to date. There must also be a plan for ensuring access to IT systems and their operating functions during and after a security incident.
- The use of multi-factor authentication, continuous authentication solutions, voice, video, and text encryption, and encrypted internal emergency communication, when appropriate.
- Security around supply chains and the relationship between the company and direct supplier. Companies must choose security measures that fit the vulnerabilities of each direct supplier. And then companies must assess the overall security level for all suppliers.
What do the fines look like?
NIS1 imposed penalties on Operators of Essential Services (OES) and Digital Service Providers (DSPs) for failing to comply with its regulations. NIS2, however, escalates the severity of penalties for non-compliance, introducing potential fines up to 10% of an entity’s yearly revenue.
Specifically, for essential entities, NIS2 allows for administrative fines reaching €10,000,000 or a minimum of 2% of the entity’s total global turnover from the last financial year, depending on which is greater.
For important entities, the directive sets fines up to €7,000,000 or at least 1.4% of the entity’s total worldwide turnover from the previous fiscal year, again applying whichever is the larger amount.
Furthermore, NIS2 places a significant emphasis on the accountability of senior management for their organization’s cybersecurity. If management fails to implement adequate security measures, they can be held personally liable. This includes the obligation to publicly disclose the breach, specifying the individuals responsible and detailing the nature of the incident. In extreme situations, management members could face temporary disqualifications from their roles.
What Stroople can do for you?
Prepare for NIS2 today and secure your digital operational resilience tomorrow
Stroople is ready to help your company prepare for NIS2. Whether you need gap analysis of what you lack in order to comply with the legislation, risk assessment of your cybersecurity, or implementation of systems such as Zero Trust cybersecurity, Stroople’s cybersecurity experts can help you.

NIS2
Our approach
The evolving landscape necessitates that organizations develop the ability to adeptly and efficiently prepare for and navigate through cyber crises. Depending on your organization’s level of maturity and the capabilities you aim to achieve, the following activities emerge as key focus areas for safeguarding critical infrastructure and ensuring adherence to the NIS Directive and its subsequent repeal.
Stroople possesses the expertise and resources needed to guide you through your compliance journey. Our holistic approach includes the following steps:

-
Gap Analysis: We evaluate your organization’s current positioning against the NIS2 requirements, pinpointing vulnerabilities and compliance gaps.
-
Cybersecurity Strategy and Governance Framework: We formulate a comprehensive strategy that aligns cybersecurity efforts with your business goals, underpinned by a governance framework that clarifies roles and establishes escalation procedures.
-
Information Security Management: We implement stringent security practices encompassing data transmission, encryption, access management, and strategies for incident reporting and response.
-
Supply Chain Security Enhancement: We elevate security protocols for your partners and suppliers with rigorous compliance standards, regular evaluations, and secure practices in technology procurement and development.
-
Testing, Assessment, and Improvement: We ensure the continuous improvement of your systems through effectiveness reviews, periodic testing, and the proactive upgrading of security protocols to maintain compliance and safeguarding measures.
